بسم الله الرحمن الرحيم
التحليل الوظيفى
TOR
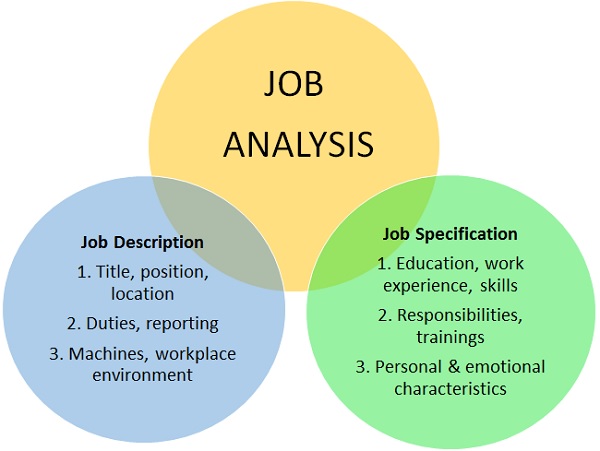
SOC Analyst (Level 3) Job Analysis
Job Overview:
A Level 3 SOC Analyst leads the Security Operations Center, managing critical incidents, overseeing incident response strategies, and optimizing SOC processes to enhance organizational security.
Key Responsibilities:
Leadership and Management:
- Oversee the SOC team and ensure 24/7 operational readiness.
- Lead investigations into high-priority incidents and breaches.
Process Optimization:
- Create and maintain incident response playbooks and procedures.
- Develop and implement SOC policies to improve detection capabilities.
Collaboration and Reporting:
- Coordinate with Red and Blue Teams to strengthen defenses.
- Present findings and recommendations to senior management.
Daily Tasks:
- Supervise SOC operations and ensure efficient incident handling.
- Review incident reports and ensure thorough analysis.
- Lead post-incident reviews and recommend enhancements.
Skills:
1. Computer Skills:
- Advanced SIEM management and integration.
- Threat intelligence tools and forensic platforms.
2. Language Skills:
- Concise reporting for C-level executives.
- Strong communication for guiding team members and coordinating responses.
3. Job Technical (Functional) Skills:
- Deep expertise in intrusion detection and advanced forensics.
- Proficiency in threat modeling and incident response playbooks.
4. Interpersonal Skills:
- Leadership: Managing teams in high-pressure scenarios.
- Strategic Thinking: Anticipating future threats and preparing defenses.
- Mentorship: Training and developing junior SOC staff.
Job Specifications:
- Education: Bachelor’s or Master’s degree in Cybersecurity, IT, or related field.
- Experience: 6+ years in SOC leadership or incident response.
- Certifications: CISSP, GCIA, CISM.
Performance Metrics:
- Efficiency and effectiveness of SOC operations.
- Response times for high-priority incidents.
- Implementation of improved detection and response strategies.